Facial Recognition Bans Spread Globally
A ruling last week in Australia makes using facial recognition to combat fraud almost impossible and is the latest example of global regulators’ growing disapproval of biometric technology in retail environments.
The Office of the Australian Information Commissioner (OAIC) determined that Kmart Australia Limited had violated the country’s Privacy Act 1988 when it used facial recognition to prevent return fraud and theft.

Kmart stores in Australia had used facial recognition technology to catch fraudsters. Image: Wesfarmers.
Kmart and Bunnings
At question was a Kmart pilot program that had placed facial recognition technology (FRT) in 28 of the company’s retail locations from June 2020 through July 2022.
The company created a face print, if you will, of every shopper entering one of the pilot program stores. When a customer returned an item, Kmart’s system would compare that person’s face print to a list of known thieves and fraudsters.
Kmart argued that the technology aimed to thwart return fraud and protect its employees, which thieves had frequently threatened. Biometrics, however, represent a special category of privacy protection in Australia.
The case was similar to a November 2024 OAIC determination against Bunnings, a home-improvement retailer, for using FRT to identify criminals. Australian conglomerate Wesfarmers Limited owns Kmart Australia, Bunnings, and other retail chains, including Target Australia.
FRT Challenges
The OAIC stated that its finding is not a ban on FRT, but its conditions make using the technology challenging, if not impossible.
For example, an Australian retailer would need consent before employing FRT, and the thieves stealing items to attempt return fraud would almost certainly refuse.
Kmart had disclosed FRT in a sign at the front of each pilot store, which read, “This store has 24-hour CCTV coverage, which includes facial recognition technology.” But this notice did not establish consent according to the OAIC.
Asking would-be criminals for permission to use facial recognition has the same effect as banning it, given the current state of the technology.
GDPR
The OAIC’s Kmart decision regarding explicit consent aligns with other privacy regulations and rulings.
For example, many privacy experts note that Article 9 of the European Union’s General Data Privacy Regulation, which covers the processing of special categories of personal data, requires explicit consent for the use of FRT.
FTC vs. Rite Aid
In the United States, there are instances of rulings against FRT and the use of biometric data.
In a 2023 determination, the U.S. Federal Trade Commission prohibited Rite Aid Pharmacy from using FRT and other automated biometric systems for five years.
The agency argued that Rite Aid had not taken sufficient measures to prevent false positives and algorithmic racial profiling.
Illinois BIPA
The Illinois Biometric Information Privacy Act was enacted in 2008 and is, perhaps, the most stringent biometric privacy law in the nation.
The BIPA requires businesses to provide written notification of the use of biometric data and obtain shoppers’ written consent. The law permits individuals to sue for violations, and has resulted in many cases against retailers, such as:
- A 2022 lawsuit alleges that Walmart’s in-store “cameras and advanced video surveillance systems” secretly collect shoppers’ biometric data without notice or consent.
- A March 2024 class-action lawsuit against Target alleges the retailer used FRT to identify shoplifters without proper consent.
- A class-action lawsuit filed in August 2025 alleges that Home Depot is illegally using FRT at its self-checkout kiosks.
M•A•C Cosmetics
From the retail and ecommerce perspective, the most concerning BIPA lawsuit may be Fiza Javid v. M.A.C. Cosmetics Inc. The class-action suit, filed in August 2025, is not concerned with crime fighting but with virtual try-on technology.
The complaint notes that M•A•C’s website asks shoppers to upload a photo or enable live video so that it can detect someone’s facial structure and skin color. Plaintiff Fiza Javid asserts the feature would require BIPA’s written consent and is therefore in violation of the Illinois law.
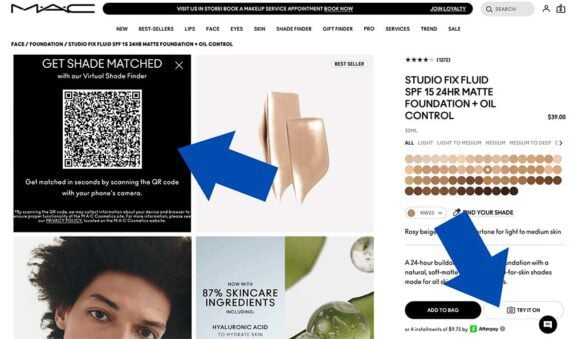


M•A•C Cosmetics offers tools for virtual try-on and skin color identification.
M•A•C’s virtual makeup try-on tools enhance the experience for shoppers and almost certainly improve ecommerce conversion rates.
The merits of the case are pending, yet BIPA has already spawned virtual try-on cases, including:
- Kukovec v. Estée Lauder Companies, Inc. (2022).
- Theriot v. Louis Vuitton North America, Inc. (2022).
- Gielow v. Pandora Jewelry LLC (2022).
- Shores v. Wella Operations US LLC (2022).
Engagement and Enforcement
AI-driven facial recognition and biometric technology are among the most promising trends in retail and ecommerce.
The technology has the potential to reduce fraud, deter theft, and support criminal prosecutions. A 2023 article in the International Security Journal estimated that facial biometrics could reduce retail shoplifting by between 50% and 90% depending on location and use.
Moreover, biometrics can improve online and in-store shopping with virtual try-on tools. Some merchants have reported a 35% increase in sales conversions when virtual shopping is available.
The question is how privacy regulations and rulings, such as last week’s Kmart decision, ultimately impact its use.





